Welcome to "Spotlight on Essential 8." In this guide, we will shed light on the Australian government's Essential 8 control framework, its benefits, and provide a recommended approach for the adoption of this baseline cybersecurity framework.
What is the Essential 8 Control Framework:
The Essential 8 is a baseline cybersecurity control framework developed by the Australian Signals Directorate (ASD) and Australian Cyber Security Centre (ACSC). It aims to assist organisations in mitigating the most prevalent cyber threats faced today. The framework consists of eight essential strategies that serve as a recommended minimum baseline and when implemented effectively, can significantly enhance an organisation's cybersecurity posture.
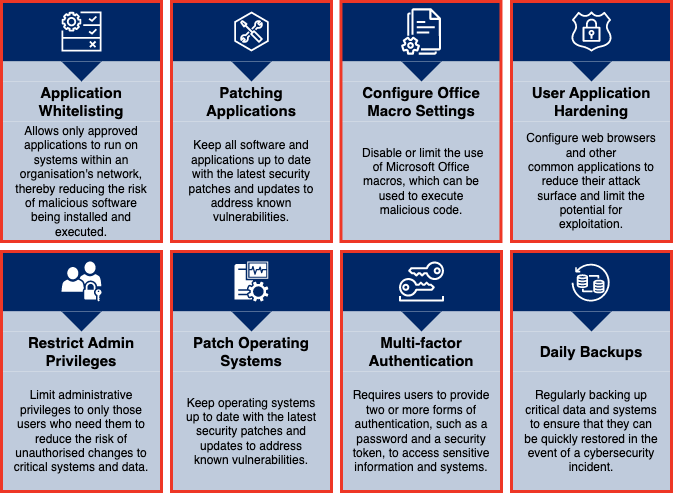
Here's a brief outline of each of the Essential 8 controls within the framework:
Benefits of Implementing the Essential 8:
Each control has been selected to provide a specific benefit aligned to 1 or more common risk scenarios.
| Control | Benefit |
| Application Whitelisting | Ensures that only approved and authorised applications are allowed to run on systems, reducing the risk of malicious software execution. |
| Patch Applications | Regularly applying patches and updates to operating systems, software, and firmware helps address known vulnerabilities and protect against cyber-attacks. |
| Configure Microsoft Office Macro Settings | Adjusting settings within Microsoft Office products helps mitigate the risk associated with malicious macros, a common vector for malware distribution. |
| User Application Hardening | Implementing security measures such as disabling unnecessary features and blocking malicious content in web browsers and email clients minimises the risk of cyber threats. |
| Restrict Administrative Priveleges | Limiting administrative privileges to authorised personnel reduces the likelihood of unauthorised access and minimises the impact of potential breaches |
| Patch Operating Systems | Regularly applying security patches and updates to operating systems helps address known vulnerabilities and protect against exploitation by cyber threats. |
| Multi-factor Authentications | Adding an extra layer of security through multi-factor authentication (MFA) helps protect sensitive information by requiring users to provide multiple forms of identification. |
| Daily Backups | Regularly backing up critical data and verifying its integrity allows for timely restoration in case of data loss or a ransomware incident. |
Additionally, the Essential 8 controls, when implemented collectively and effectively, provide a solid foundation for improving an organisation's cybersecurity resilience and reducing the risk of cyber incidents.
- Risk Mitigation: By adopting the Essential 8 framework, organisations can identify and mitigate common cyber threats, reducing the likelihood of successful attacks.
- Proactive Defence: The Essential 8 focuses on proactive measures, enabling organisations to prevent cyber incidents rather than merely responding to them.
- Alignment with Best Practices: The framework aligns with industry best practices and is regularly updated to address emerging threats, ensuring its ongoing relevance.
- Regulatory Compliance: Implementing the Essential 8 helps organisations meet compliance requirements, including those outlined in the Australian Government Information Security Manual (ISM).
A Comprehensive Approach: Assess, Design, Implement, Operate
To effectively implement the Essential 8 control framework and enhance your organisation's cybersecurity defences, it is crucial to follow a systematic approach. The approach outlined below, consisting of four key stages - Assess, Design, Implement, and Operate - provides a structured framework for successful assessment and implementation.
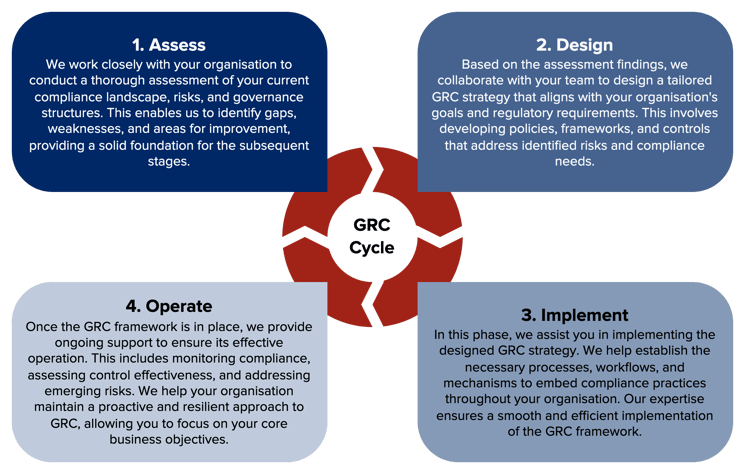
Assess:
The first stage of the approach involves conducting a comprehensive assessment of your organisation's current cybersecurity measures. This assessment serves as a baseline to identify gaps, vulnerabilities, and areas of improvement in relation to the Essential 8 controls. An Essential 8 assessment will typically consist of the following activities;
- Conduct a thorough assessment of your organisation's current cybersecurity measures, including policies, controls, and systems.
- Identify any gaps or vulnerabilities in relation to the Essential 8 controls.
- Evaluate the effectiveness of existing controls and their alignment with the recommended strategies.
- Assess the risk profile of your organisation and prioritise areas that require immediate attention.
By understanding the existing state of your cybersecurity posture, you can make informed decisions and prioritise actions to mitigate risks effectively.
Design:
Once the assessment stage is complete, the next step is to design a comprehensive plan for implementing the Essential 8 controls. This stage involves translating the assessment findings into actionable steps that align with your organisation's goals and risk profile. The design phase typically includes the following activities;
- Based on the assessment findings, design a comprehensive plan for implementing the Essential 8 controls.
- Determine specific actions and steps required to address the identified gaps and vulnerabilities.
- Define the desired state of each control and establish measurable goals and objectives.
- Develop policies, procedures, and guidelines that align with the Essential 8 framework.
By designing a well-thought-out plan, you can ensure that the Essential 8 controls are tailored to your organisation's specific needs and provide a solid foundation for enhancing your cybersecurity defences.
Implement:
With the design phase complete, it's time to put the plan into action and implement the identified controls and measures. This stage typically involves;
- Execute the designed plan by implementing the identified controls and measures.
- Allocate appropriate resources, including personnel and technology, for the successful implementation of each control.
- Provide necessary training and awareness programs to ensure employees understand their roles and responsibilities in adhering to the controls.
- Regularly communicate progress and updates to stakeholders and obtain their support for the implementation process.
By effectively implementing the Essential 8 controls, you establish a proactive security posture that mitigates risks and protects your organisation from cyber threats.
Operate:
Once the Essential 8 controls are implemented, it is essential to establish an operational framework to maintain their effectiveness over time. The operate stage focuses on ongoing monitoring, evaluation, and improvement of the implemented controls and will typically consist of the following activities;
- Establish mechanisms to monitor and measure the effectiveness of the implemented controls.
- Continuously review and assess the operation of each control to identify any potential weaknesses or areas for improvement.
- Stay informed about emerging threats and updates to the Essential 8 framework.
- Conduct periodic audits and assessments to ensure ongoing compliance and effectiveness of the controls.
- Regularly report on the status of the Essential 8 controls to management and stakeholders.
- Maintain a culture of cybersecurity awareness and encourage ongoing training and education for employees.
Operating the controls requires continuous communication, reporting, and collaboration with stakeholders to maintain a robust cybersecurity posture and foster a culture of security within the organisation.
By following this Assess, Design, Implement, Operate approach, you can effectively assess your organisation's cybersecurity posture, design a tailored plan based on the Essential 8 controls, implement the necessary measures, and establish a framework for ongoing operation and improvement. This systematic approach ensures a comprehensive and sustainable implementation of the Essential 8 controls, enhancing your organisation's resilience against cyber threats.
Conclusion:
By embracing the Essential 8 control framework, organisations can establish a solid baseline that serves as a minimum recommended cybersecurity position. Implementing these controls helps organisations strengthen their cybersecurity defences, reduce the risk of successful attacks, and improve their overall resilience. Achieving this baseline provides a solid foundation for building further cyber defences and increasing maturity in your organisation's security posture.
While the Essential 8 provides a minimum position, it also serves as a launching pad for organisations to enhance their cyber defences and maturity. Organisations can leverage the established baseline to further customise and tailor cybersecurity measures to their specific needs, industry requirements, and risk landscape. This approach allows for continuous improvement and adaptation to evolving cyber threats, ensuring that your organisation stays ahead of potential risks.
Contact us today to explore how our specialist cybersecurity consulting services can assist you in implementing the Essential 8 controls, establishing a strong cybersecurity baseline, and advancing your organisation's cyber defence maturity. Together, we can elevate your cybersecurity posture to safeguard your critical assets, data, and operations from ever-evolving cyber threats.

June 19, 2023